Danielle “DJ” Jablanski recently joined STV’s growing cybersecurity practice as the organization’s new cybersecurity consulting program lead, specializing in Operational Technology (OT).
For nearly a decade, Jablanski has been a leading voice in OT cybersecurity, demonstrating a deep understanding of the evolving threats facing critical infrastructure. She most recently led OT strategy in the Office of the Technical Director with the federal Cybersecurity and Infrastructure Security Agency (CISA) and previously worked as a cybersecurity strategist at a major OT cybersecurity solution provider.
In this interview, Jablanski discusses how she’s leveraging her experience to support STV’s clients across all markets, as well as her overall approach and guidance on navigating some of the most pressing challenges in OT cybersecurity today.
1. How does your recent experience with CISA allow you to best serve infrastructure clients at STV?
My strategic focus at CISA was centered around enhancing the agency’s role as a service provider to owners and operators of OT and industrial control systems. With that understanding of the available assessments and control capabilities and state and federal response capacity, as well as relationships with additional sector risk management agencies, I can assist our clients with building robust and effective security programs that they can then further develop and maintain. The bottom line for the markets we serve will be continuous improvement and underpinning the requirement to operate under, or despite, cyber compromise.
2. You’ve described yourself as an analyst first. How has that perspective shaped your approach to OT cybersecurity?
Being an analyst at heart keeps me focused on asking the right questions and always being overprepared. Not just considering, “what could happen?” but “how could it happen,” and “what are the plausible impacts?” In OT environments, that mindset is crucial. You often work with asset owners who are inundated with information, multiple tools, and shifting priorities. My role is to help them cut through the noise and focus on what truly matters: understanding their systems, preparing for the right scenarios, and getting the most out of tools and capabilities.

3. Why do asset inventory and third-party risk remain challenging for asset owners?
Cybersecurity has become everything, everywhere, all at once. Overcoming these challenges requires sustained, structural changes, not quick fixes. For asset inventory, it’s not just about listing devices. It’s also about understanding how everything connects and communicates, as well as where vulnerabilities matter most and how to prioritize decisions and actions. On third-party risk, the complexity is even greater. Asset owners are expected to vet every technology component in use: hardware, software, firmware, applications, and the vendor’s vulnerability management. For security, it’s also, “I have this solution, but now they’re offering an OT solution; how do I validate that capability?” It’s a visibility issue, a risk of ownership issue, and a bandwidth issue. Even with unlimited financial resources and the best security stack, most organizations aren’t staffed correctly to navigate this challenge. They need trusted advisors and partners to make informed decisions about their cybersecurity risks, vendors, solutions, and more, just like any other major project.
4. How can STV help agencies find the balance between being “too in the weeds” or thinking “too high level” about cybersecurity?
The sweet spot is operational relevance. You can’t start with abstract frameworks and hope they translate or buy shiny tools and hope they are silver bullets. At the same time, you can’t get stuck on isolated scenarios, TTPs or vulnerabilities without understanding the local, system-level implications. Even with similar systems and components, the consequences of an attack on a small utility in rural areas are likely different than those that occur at an airport in a major metro. It is essential to map out scenarios, the interdependence of critical systems and functions, and compounding and cascading factors. We have to explicitly understand impact analysis – the potential effects of an incident, especially in smaller communities or mission-critical facilities with less redundancy. Then, the response has to be tailored, affordable, and continuously improved.
5. How can IT and OT teams partner better within an organization?
Currently, we’re seeing many IT teams extending their security controls into OT environments, sometimes with good intentions, but often without the necessary operational nuance. The result? A security tool that grabs data from an OT network but doesn’t support decision-making or a detection tool in OT networks that sees a lot of IT signatures. We need to shift the conversation from convergence to context: how do we secure systems based on how they actually operate? What tools and data do we already have to help us navigate effects-based analysis, rather than focusing on every potential scenario for an adversarial cyberattack? We must work together to identify the potential attack paths and the fault tolerance in systems so we can plan for both the worst-case scenario and the scenario a team is least prepared to respond to. The difference between a “bad day” and an unprepared one represents significant potential for loss.
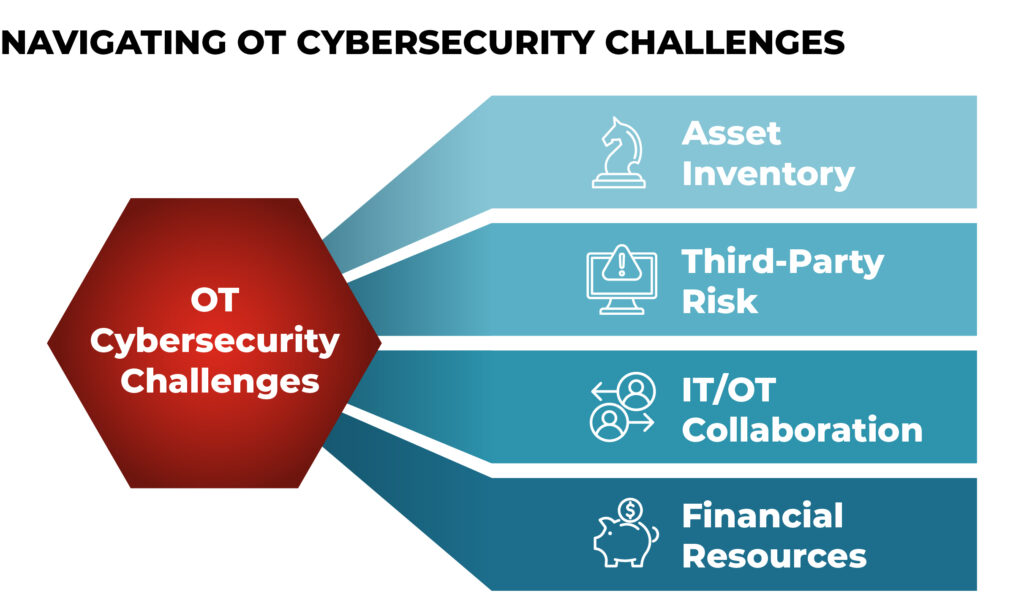
6. What’s your take on the perception that there’s a lack of financial resources to invest in OT security?
It’s more about building programs than purchasing tools. Organizations make massive capital investments in other areas, but security isn’t always built into the procurement language. The better question is: how do we start this security journey? What preventative measures will shore up the majority of threats we’ve seen before and know how to handle? How do we embed cybersecurity into the design phase, not bolt it on afterward? It’s not about buying the most expensive solution or even conducting the most in-depth assessment – it’s about making smart, intentional decisions early on that leverage all the tacit knowledge and specific context each organization can bring to bear, testing assumptions and investing in people and technology.








